Cisco Firewall Interface
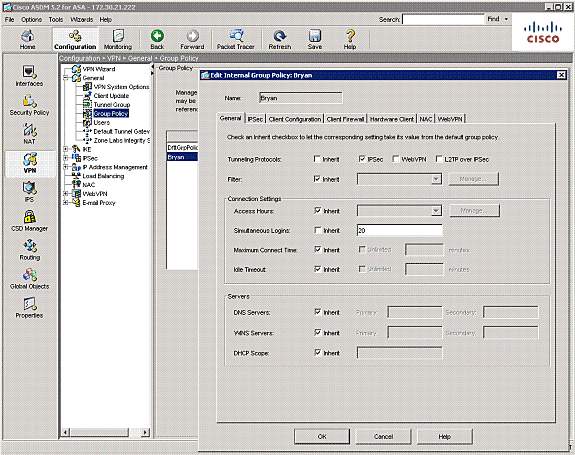
Most Common L2l And Remote Access Ipsec Vpn Troubleshooting Solutions Cisco
Cisco Asa Firewall Hardening Dionach
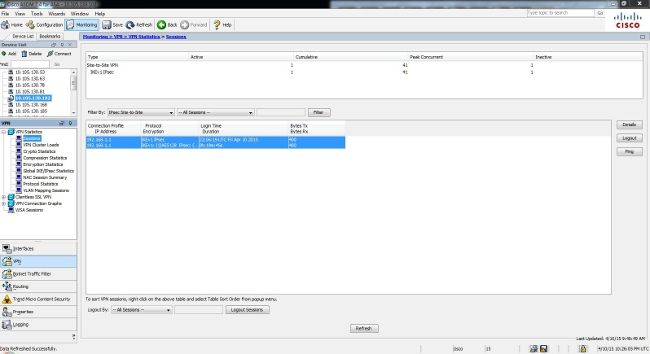
Configure Ikev1 Ipsec Site To Site Tunnels With The Asdm Or Cli On The Asa Cisco

How To Configure Cisco Pix Firewall Router Switch Blog
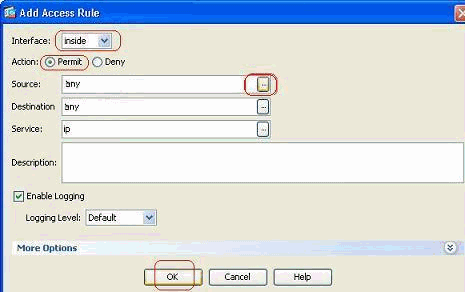
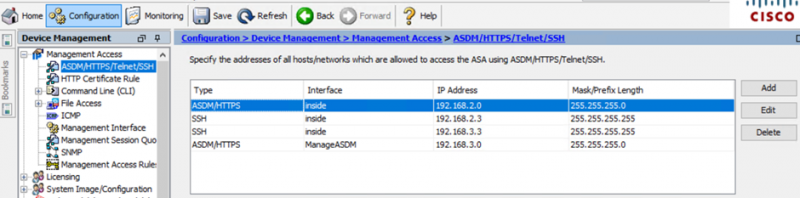
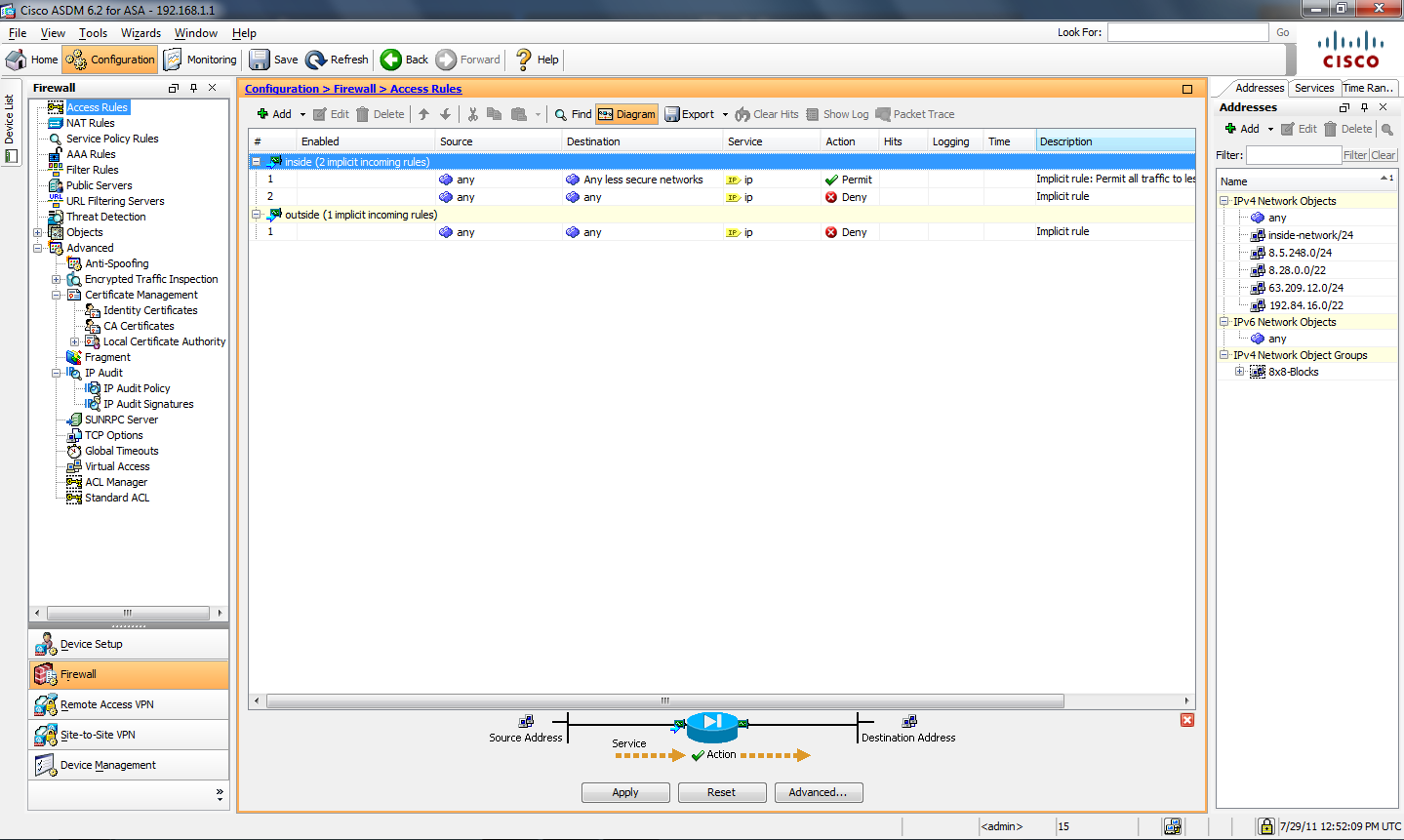
Asa 8 X And Later Add Or Modify An Access List Through The Asdm Gui Configuration Example Cisco

Cisco Asa Lan Tech Network Management
Cisco PIX firewall Basics A Cisco PIX firewall is meant to protect one network from another There are PIX firewalls for small home networks and PIX firewalls for huge campus or corporate networks In this example, we will be configuring a PIX 501 firewall.
Cisco firewall interface. Basic Guidelines for setting Internet through the Cisco ASA firewall At first we need to configure the interfaces on the firewall!— Configure the outside interface interface GigabitEthernet0/0 nameif outside securitylevel 0 ip address !— Configure the inside interface interface GigabitEthernet0/1 nameif inside. Cisco ASA firewalls are anything but basic But don’t be put off by their complexity Getting them up and running can be done in a short space of time Let’s start off with our interfaces, and how they relate to firewall function A firewall separates traffic between different areas. When the firewall has a large L2 VLAN attached and hosts are using the firewall interface as a Default route, and further it has routes to networks via the same connected interface, the firewall can allow this traffic under other correct configuration conditions (NAT and ACL).
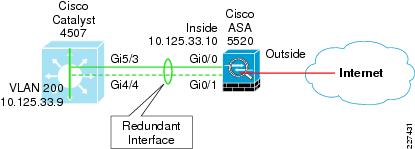
Cisco ASA Redundant Interface Configuration In addition to devicelevel failover as we’ve discussed above, you can also configure interface redundancy on the same chassis of a Cisco ASA firewall Basically you can create a logical interface pair bundle (called “ interface redundant “) in which you include two physical interfaces. Description Configuring IP Addresses Security Level and NameIf Permitting ICMP Static Route configuration PacketTracer command in ASA Enabling Telnet on Cisco ASA Enabling SSH on Cisco ASA Interface ACL Global ACL Object Group Object creation Active Standby Failover Transparent Mode Multiple Bridge. From the Configuration tab in Cisco ASDM, you can view the list of interfaces by selecting Device Setup > Interfaces, as shown in Figure 31 Figure 31 Using ASDM to View a List of Interfaces From the CLI, you can see a list of the physical firewall interfaces that are available by using the following command ciscoasa# show version.
Cisco offers a wide range of products and networking solutions designed for enterprises and small businesses across a variety of industries. The interface for the 4400 series WLC and 5500 series WLC is similar. To check the name of your interfaces run the command SHOW RUN INTERFACE This will return a list of all the interfaces on the firewall Check for a line under each interface called NAMEIF This is the name of the interface For example, you may have a DMZ network connected to a physical interface that is listed as NAMEIF DMZ Let’s say you.
One of the advantages of the Cisco ASA firewall is that you can configure multiple virtual interfaces (subinterfaces) on the same physical interface, thus extending the number of security zones (firewall “legs”) on your network Each subinterface must belong to a different Layer2 VLAN, with a separate Layer3 subnet. Understanding the functionality of each logical interface is crucial for the correct setup and deployment of any Cisco WLCbased wireless network The WLC’s logical interfaces are used to help manage the Wireless SSIDs broadcasted by the access points, manage the controller, access point and user data, plus more. All Cisco IOS router models with release 124(6)T and above support this with the exception of newer ASR models and IOS XE which only supports the zone based model Setting up a simple two interface firewall Here’s the task Inside Network Interface /24;.
Cisco firewalls define a specific interface as being the Management interface This designation is defined by configuring the managementonly command on the specific interface By default the physically defined Management interface has this command defined This interface is used for inband access to a Cisco firewall. One of the advantages of the Cisco ASA firewall is that you can configure multiple virtual interfaces (subinterfaces) on the same physical interface, thus extending the number of security zones (firewall “legs”) on your network Each subinterface must belong to a different Layer2 VLAN, with a separate Layer3 subnet. Cisco ASA and Firebox BOVPN Virtual Interface Integration Guide see BOVPN Virtual Interfaces Configure the Cisco ASA In our example, we configure a Cisco ASA 5506X Select Configuration > Firewall > Objects > Network Objects/Groups Click Add > Network Object.
Cisco ASA Firewall Best Practices for Firewall Deployment The document provides a baseline security reference point for those who will install, deploy and maintain Cisco ASA firewalls It describes the hows and whys of the way things are done It is a firewall security best practices guideline. Interface GigabitEthernet0/0 nameif OUTSIDE securitylevel 0 ip address !. Switch1(config)#interface fastEthernet 0/1 When working with switches, the first interface is numbered one, whereas when you work with most other Cisco devices, you find the first interface is zero Set the specifics of the network connection or use the Auto settings for medium dependent interface crossover (MDIX), Duplex, and Speed settings.
Cisco offers a wide range of products and networking solutions designed for enterprises and small businesses across a variety of industries. Complete the following steps to determine if an outside interface is configured with a static IP address Step 1 Click Configure > Interfaces and Connections > Edit Interface/Connection Step 2 Review the IP column in the Interface list table to determine if an outside interface has a static IP addresses. Cisco ASA Firewall – Web Administration and Web VPN Cisco ASA Firewalls (ASA 5500 series) offer several ways for remote administration and management of the devices such as SSH access, Telnet access, and Web HTTP access The last one (HTTP access) makes use of the ASDM (Adaptive Security Device Manager) which is a powerful graphical application for administration and management of the firewall device.
To do this, the interface is configured to operate as a VLAN trunk link On ASA 5510 and higher platforms, each VLAN that is carried over the trunk link terminates on a unique subinterface of a physical interface On an ASA 5505, each VLAN is defined by a unique VLAN interface and can connect to physical interfaces and be carried over a VLAN trunk link. The ASDM is the main management interface for Cisco’s Adaptive Security Appliance (ASA) firewalls and is also launched through the web management interface A sample of the web interface used for managing the Cisco 2106 WLC is shown;. Earlier, I wrote an article showing how to do a VTI (Virtual Tunnel Interface) from a Cisco ASA to a Fortigate Firewall Today, I will cover a routebased VPN with a Cisco Router instead of a Cisco ASA using VTIs Where as the ASA only supports BGP with its VTI implementation, the router is a bit more flexible and allows for OSPF.
Cisco ASA 5500 Firewall ConfigurationUser Interface and Access Modes This article describes the user interface and access modes and commands associated with the operation of Cisco ASA 5500 firewall appliances We assume that you know how to connect to the appliance using a console cable (the blue flat cable with RJ45 on one end, and DB9 Serial on the other end) and a Terminal Emulation software (eg HyperTerminal), and how to use basic Command Line Interface. Interface Configuration in Cisco ASA (Transparent Mode) In this section, we will discuss about the interface configuration for all models in transparent firewall mode The default operational mode of Cisco ASA is Routed To change the firewall operational mode to transparent, run the command as shown below. From the Configuration tab in Cisco ASDM, you can view the list of interfaces by selecting Device Setup > Interfaces, as shown in Figure 31 Figure 31 Using ASDM to View a List of Interfaces From the CLI, you can see a list of the physical firewall interfaces that are available by using the following command ciscoasa# show version.
All interfaces on a Cisco PIX Firewall are shut down by default and are explicitly enabled by the interface command The basic syntax of the interface command is as follows interface hardware_id hardware_speed shutdown Table 61 describes the command parameters for the interface command Table 61 interface Command Parameters. This time I noticed some speed/duplex interface errors when trying to configure the management interface What fixed it was switching the Ciscoprovided interface types in the OVA (E1000) to VMXNET3 interfaces So it seems to me that Cisco bundled the image with interfaces that don't support it/it doesn't support. Its a Basic configuration of Cisco ASA firewall As we know that Firewall use to secure our internal Network from External network Hackers try to access internal network from internet (external Network) so that we need to deploy Firewall in Network we will configure firewall with scenario based Cisco ASA Firewall Interfaces Configuration.
All Cisco IOS router models with release 124(6)T and above support this with the exception of newer ASR models and IOS XE which only supports the zone based model Setting up a simple two interface firewall Here’s the task Inside Network Interface /24;. By default, interface Ethernet0/0 is assigned to VLAN 2 and it’s the outside interface (the one which connects to the Internet), and the other 7 interfaces (Ethernet0/1 to 0/7) are assigned by default to VLAN 1 and are used for connecting to the internal network. Download CISCO Firewall IOS to the Router using TFTP Insert CDROM Go to E\Images\1 Look at Info File using Notepad RILidf for the correct OS We used aaa1314bin Cisco 2600 IOS IP/FW Feature Set 1(7)XK1 Copy aaa1314bin to TFTP directory C\TFTP\root Load Image to Router firebox> enable firebox2# copy tftp flash.
The ASDM is the main management interface for Cisco’s Adaptive Security Appliance (ASA) firewalls and is also launched through the web management interface A sample of the web interface used for managing the Cisco 2106 WLC is shown;. When you 'shutdown' an ASA interface, the status is 'administratively shutdown' but physically the link is still 'up' (link LED on the ASA and the switch it connects to!) Why?. Firewall interfaces are referenced by their hardware index and their physical interface names Example 31 lists the physical interfaces in an ASA 5510 Ethernet0/0 through 0/3 and Management0/0 are builtin interfaces, while GigabitEthernet1/0 through 1/3 are installed as a 4GESSM module Example 31.
Cisco ASA 5500X Firewall Security Levels Explained This article describes the security levels concept as used in the Cisco ASA firewall appliance The following information applies to both the older 5500 series and the newer 5500X series of appliances A Security Level is assigned to interfaces (either physical or logical subinterfaces) and it is basically a number from 0 to 100 designating how trusted an interface is relative to another interface on the appliance. A Cisco IOS firewall is a specialized feature of Cisco IOS Software that runs on Cisco routers It is a firewall product that is meant for small and mediumsized businesses as well as enterprise branch offices The earlier Cisco IOS firewall feature was called ContextBased Access Control (CBAC), which applied policies through inspect statements and configured access control lists (ACL) between interfaces The ZoneBased Policy Firewall (ZBPFW) is the newer Cisco implementation of a router. You can only use a firewall interface as the failover link Logical VLAN Interfaces You can create up to 60 VLAN interfaces If you also use VLAN subinterfaces on a firewall interface, you cannot use the same VLAN ID as for a logical VLAN interface MAC Addresses Routed firewall mode— All VLAN interfaces share a MAC address Ensure that any connected switches can support this scenario.
If an interface is named “inside”, it is automatically given a security level of 100 To view the config on all interfaces, use the show run interface command To view just one interface, use theshow run interface command and specify the interface ciscoasa(configif)# sh ru int g 0/0!. The Cisco ASA Firewall uses so called “security levels” that indicate how trusted an interface is compared to another interface The higher the security level, the more trusted the interface is Each interface on the ASA is a security zone so by using these security levels we have different trust levels for our security zones. This article is the first part of Cisco Zone Based firewall configuration It provides technology overview, configuration constructs and simple network configuration example The part 2 will provide more complex examples with NAT, DMZ, VPNs and operation of self zone Overview Cisco zonebased firewall (ZBF) is a feature of a Cisco router running IOS or Cisco Zone Based Firewall Step By.
Basic Guidelines for setting Internet through the Cisco ASA firewall At first we need to configure the interfaces on the firewall!— Configure the outside interface interface GigabitEthernet0/0 nameif outside securitylevel 0 ip address !— Configure the inside interface interface GigabitEthernet0/1 nameif inside. Other user databases are analyzed in Chapter 14, "Identity on Cisco Firewalls" Example 35 illustrates the usage of some CLI output filters To reflect the degree of trustworthiness of a given firewall interface, Cisco introduced in the early days of the PIX Firewalls the concept of Security Level The value of the Security Level (or simply. Each interface on a Cisco ASA firewall is a security zone so normally this means that the number of security zones is limited to the number of physical interfaces that we have For example, the ASA 5510 has 4 physical interfaces and often you will only see the following three security zones Inside Outside.
For interfaces that are members of the same bridge group in transparent or routed firewall mode, you can allow any IP traffic through using access rules. In this section, we will discuss about the interface configuration for all models in transparent firewall mode The default operational mode of Cisco ASA is Routed To change the firewall operational mode to transparent, run the command as shown below. Using the Management Interface of the Cisco ASA Firewall All Cisco ASA firewall models from 5510 and higher, include an extra ethernet interface for management By default, this specific interface is set to managementonly mode, which means that it can receive traffic only, but it does not allow traffic to pass through to other interfaces.
The interface for the 4400 series WLC and 5500 series WLC is similar. Other user databases are analyzed in Chapter 14, "Identity on Cisco Firewalls" Example 35 illustrates the usage of some CLI output filters To reflect the degree of trustworthiness of a given firewall interface, Cisco introduced in the early days of the PIX Firewalls the concept of Security Level The value of the Security Level (or simply. Cisco’s current generation of ASA 5500x firewalls include the option of running SourceFire IDS/IPS software on a virtual machine inside the firewall Or you could use some other vendor’s IDS/IPS The important thing is to remember that you aren’t secure just because you’ve built a rock solid ACL.
The six basic commands to configure a Cisco PIX firewall are well known nameif, interface, ip address, global, nat, and route The nameif, interface, and ip address commands are the necessary minimum to get the PIX to communicate with other devices nameif The nameif command has two big jobs to perform It names the interface and assigns a. The Cisco ASA Firewall uses so called “security levels” that indicate how trusted an interface is compared to another interface The higher the security level, the more trusted the interface is Each interface on the ASA is a security zone so by using these security levels we have different trust levels for our security zones. In this post I have gathered the most useful Cisco ASA Firewall Commands and created a Cheat Sheet list that you can download also as PDF at the end of the article I have been working with Cisco firewalls since 00 where we had the legacy PIX models before the introduction of the ASA 5500 and the newest ASA 5500X series.
Outside Network Interface (Internet) /24. Outside Network Interface (Internet) /24. An interface cannot send traffic to interfaces with a higher security level (so 50 can’t send to 100) unless there is a firewall rule that permits the specific traffic Interfaces with the same security level may be able to send traffic to each other, depending on whether samesecuritytraffic is configured.
Cisco ASA 5500 Firewall ConfigurationUser Interface and Access Modes This article describes the user interface and access modes and commands associated with the operation of Cisco ASA 5500 firewall appliances We assume that you know how to connect to the appliance using a console cable (the blue flat cable with RJ45 on one end, and DB9 Serial on the other end) and a Terminal Emulation software (eg HyperTerminal), and how to use basic Command Line Interface. Interface GigabitEthernet0/1 nameif INSIDE securitylevel 100 ip address. Cisco ASA 5500X Next Generation Firewalls with Firepower and PIX 500 Security Appliances The latest generation of ASA 5500X Series of firewalls with Firepower Services provide significantly more bang for the buck than Cisco's legacy PIX and ASA 5500 firewalls and have superseded the ASA 5500 and PIX firewalls for all new deployments.
To ensure your Cisco router or multilayer switch uses the correct interface during any tftp session, use the ip tftp sourceinterface command to specify the sourceinterface that will be used by the device The following example instructs our Cisco 3750 Layer 3 switch to use VLAN 5 interface as the source ip interface for all tftp sessions. On a router or switch, a 'shutdown' will physically shut the port down (link LEDs off). Cisco calls the ASA 5500 a “security appliance” instead of just a “hardware firewall”, because the ASA is not just a firewall This device combines several security functionalities, such as Intrusion Detection, Intrusion Prevention, Content Inspection, Botnet Inspection, in addition to the firewall functionality However, the core ASA functionality is to work as a high performance.
CISCO ASA Firewall Configuration First of All, Connect Console cable to console port, then enable command and press enter because by default no password Now type write erase command, to remove default Cisco configuration then press Y to confirm Now you will have to reboot firewall then type. Firewall mode interfaces subject traffic to firewall functions such as maintaining flows, tracking flow states at both IP and TCP layers, IP defragmentation, and TCP normalization You can also optionally configure IPS functions for this traffic according to your security policy. Cisco offers a wide range of products and networking solutions designed for enterprises and small businesses across a variety of industries.
Cisco zonebased firewall (ZBF) is a feature of a Cisco router running IOS or IOSXE It is replacement for older CBAC (ContextBased Access Control) – “ip inspect” based configuration. A Cisco firewall interface will drop any ICMP redirects it receives ICMP Unreachables Filtering with an interface access list elicits the transmission of ICMP unreachable messages back to the source of the filtered traffic Generating these messages can increase CPU utilization on the device Cisco firewalls can be configured to elicit or.
Cisco Service Ready Architecture For Schools Design Guide Security Design Design Zone For Education Cisco
Gullynetworkers Configure Rip Route Filtering On Cisco Asa Firewall

Network Fun A Security Network Engineer S Blog Cisco Firewall How A Cisco Asa L2 Firewall Works Transparent Mode

Cisco Asa Firewall Hardening Dionach

Cisco Asa Setting Up Port Forwarding Using Asdm Minecraft Example Islandearth

Mfa For Cisco Asa Vpn Via Radius Cyberark Docs

Communicating Routed Interfaces For Cisco Asa 5506 X Information Security Stack Exchange

Configuring A Warning Login Banner On Cisco Asa Firewall
Cisco Security Appliance Command Line Configuration Guide Version 7 2 Configuring Interfaces For The Cisco Asa 5505 Adaptive Security Appliance Cisco Asa 5500 X Series Firewalls Cisco
Cisco Service Ready Architecture For Schools Design Guide Security Design Design Zone For Education Cisco

Cisco Asa Integration With Authpoint
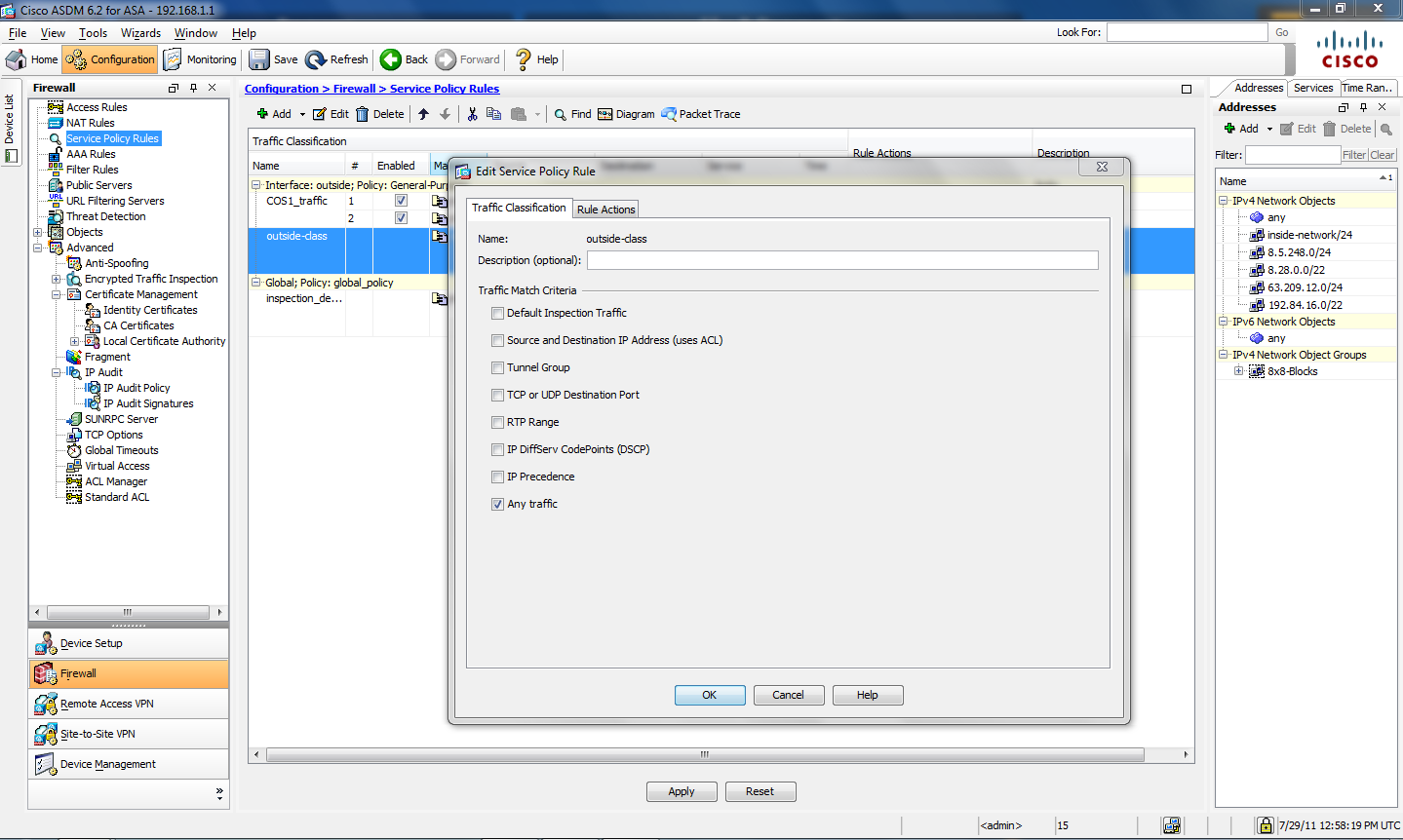
Check The Network Cisco Asa Firewall Best Practices For Firewall Deployment
How To Configure Cisco Asa 5505 Router For 8x8 Service 8x8 Support
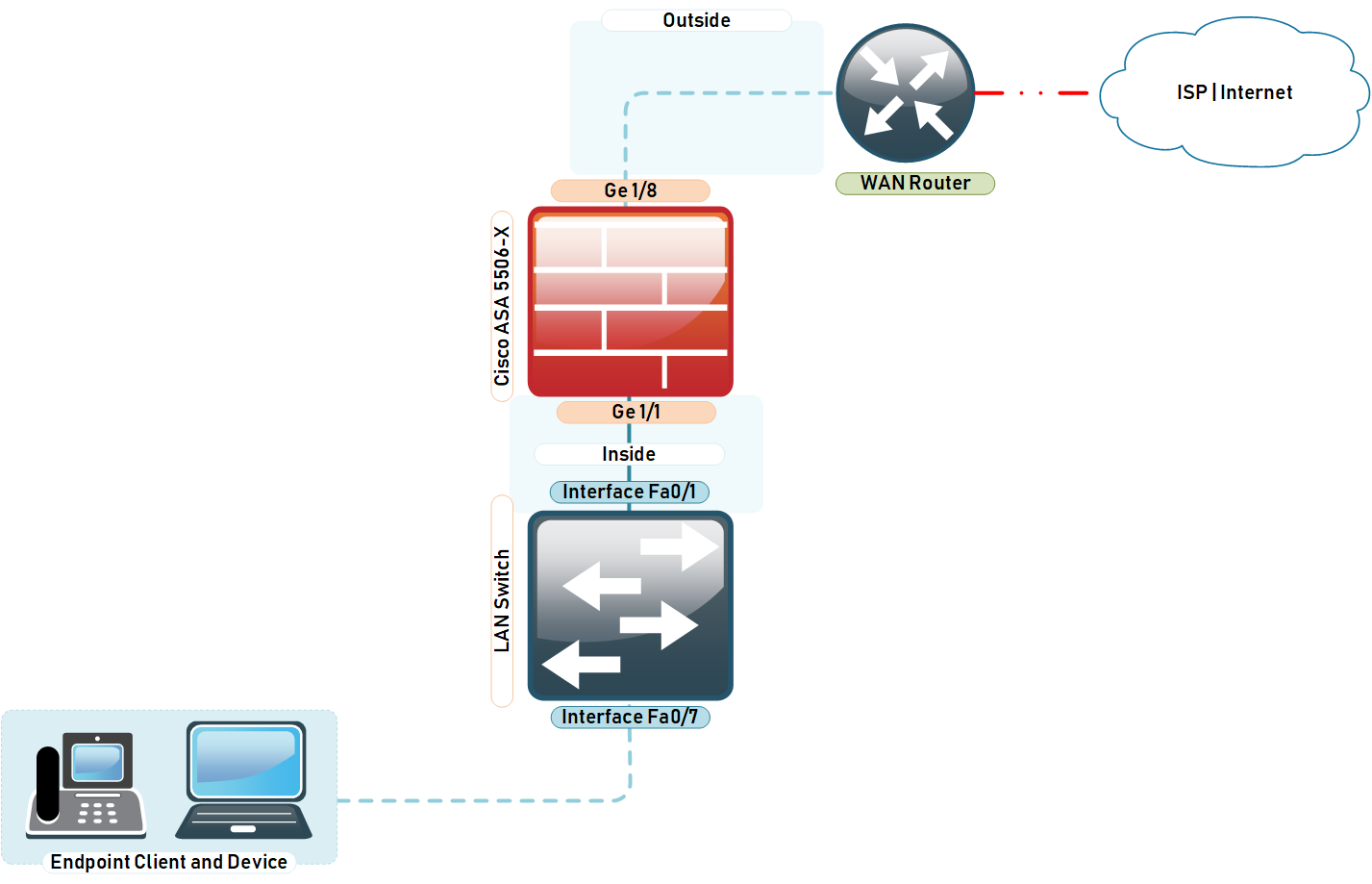
How To Configure Cisco Asa 5506 X For Internet Expert Network Consultant
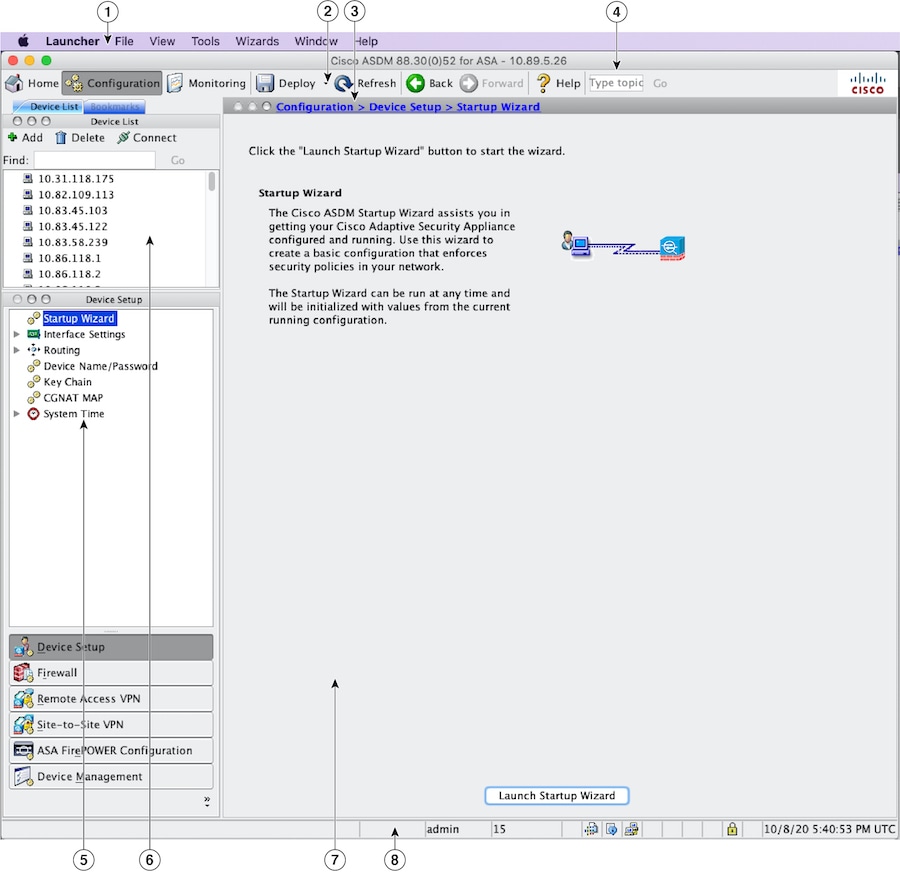
Asdm Book 1 Cisco Asa Series General Operations Asdm Configuration Guide 7 13 Asdm Graphical User Interface Cisco Firepower 4100 Series Cisco
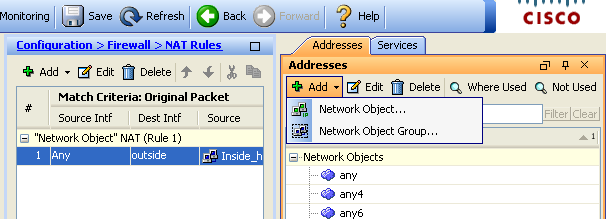
Configure Asa Version 9 X Port Forwarding With Nat Cisco

Ccna Security Packet Tracer Lab Introduction To Cisco Asa Intense School
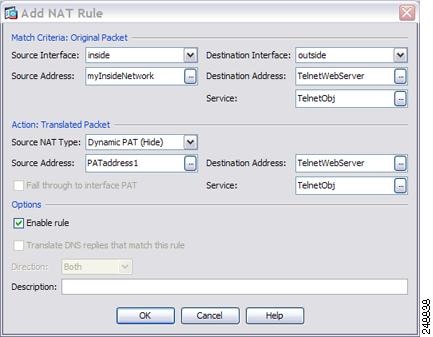
Asdm Book 2 Cisco Asa Series Firewall Asdm Configuration Guide 7 7 Nat Examples And Reference Cisco Asa 5500 X Series Firewalls Cisco
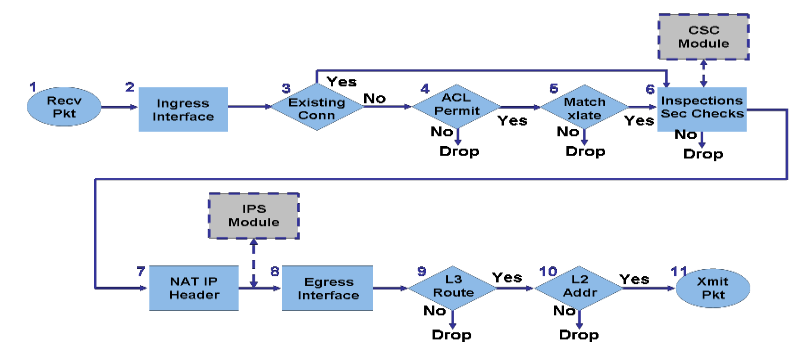
Cisco Asa Order Of Operation Tunnelsup

Configure Your Cisco Asa Or Ftd From Scratch By Ahmedshetta
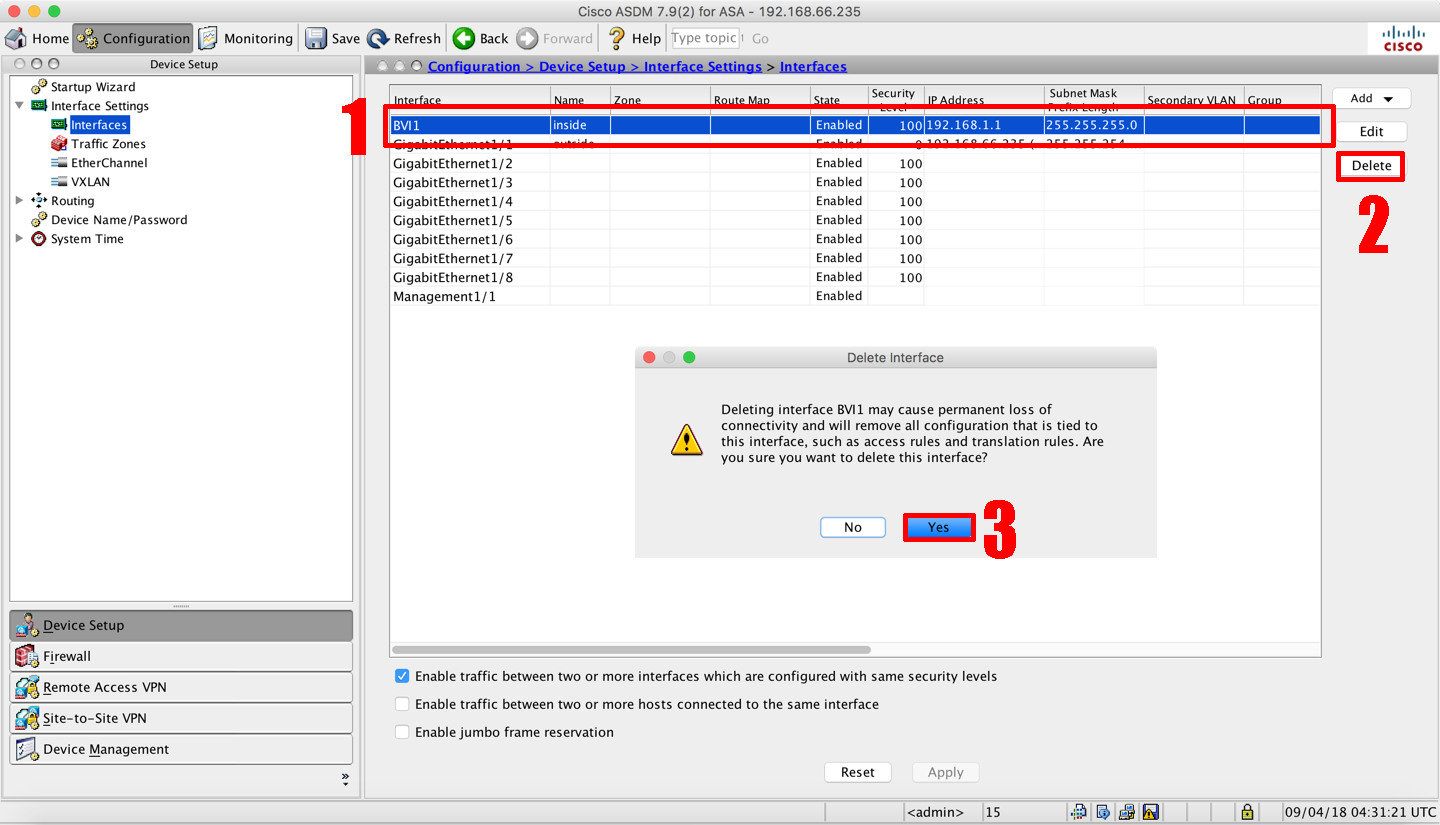
Cisco Asa 5506 X Bridged Bvi Interface Petenetlive
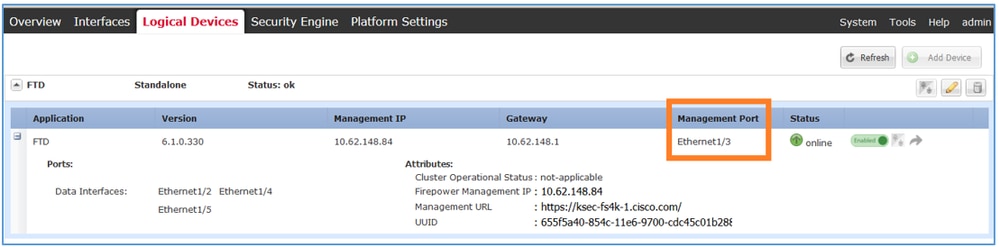
Configure Firepower Threat Defense Ftd Management Interface Cisco
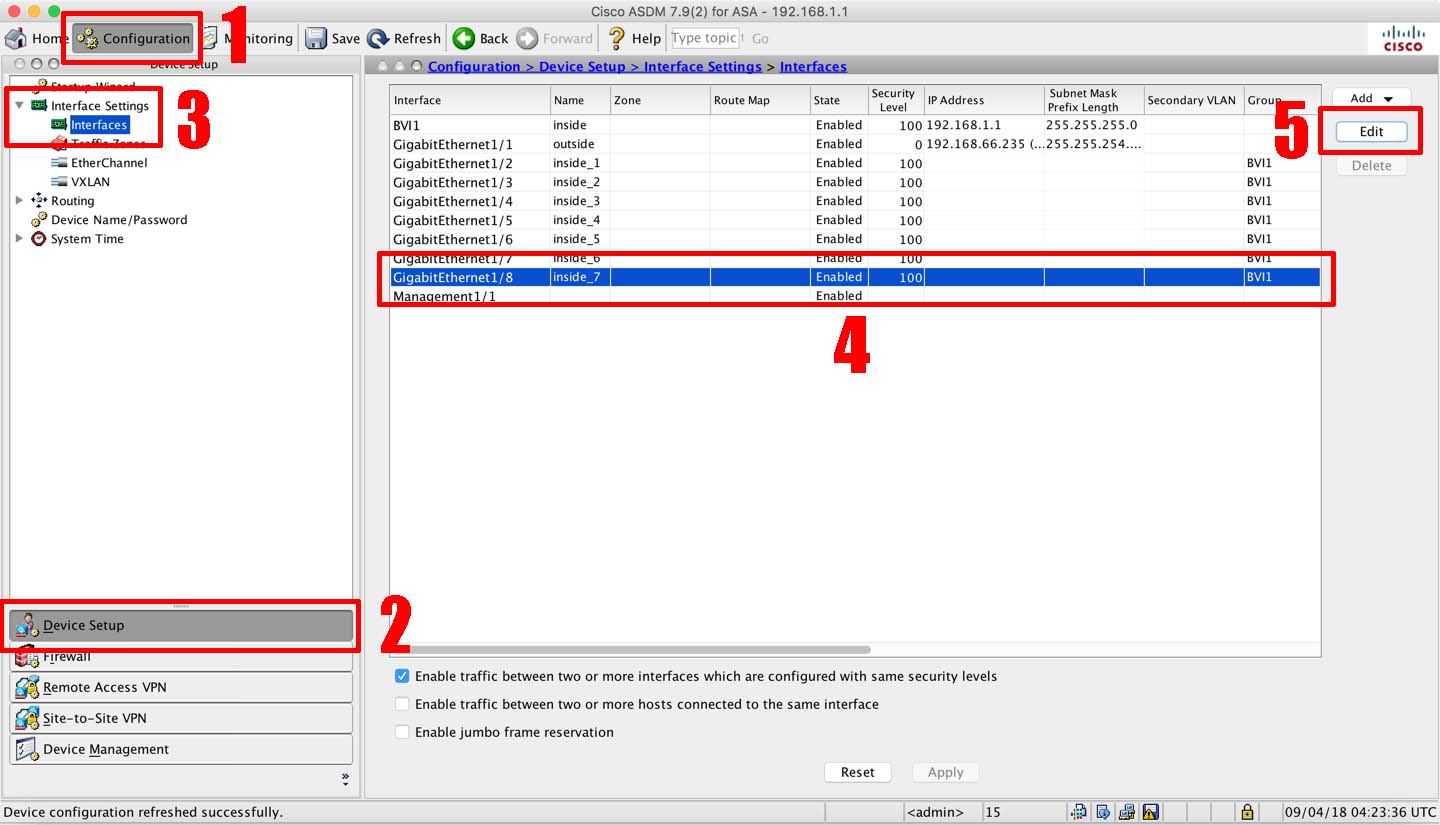
Cisco Asa 5506 X Bridged Bvi Interface Petenetlive
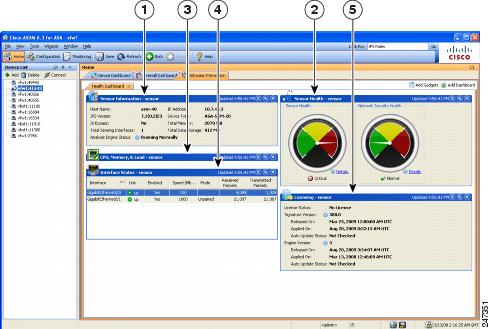
Asdm Book 1 Cisco Asa Series General Operations Asdm Configuration Guide 7 4 Asdm Graphical User Interface Cisco Asa 5500 X Series Firewalls Cisco
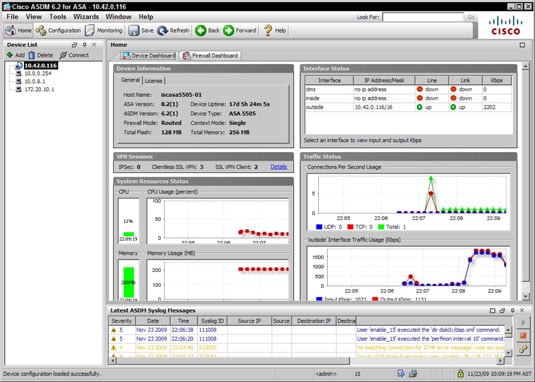
Cisco Graphical User Interface Gui Basics Dummies

Sh N S Blog Life Is Nothing Without Trying New Things Page 5
Cisco Asa 55 Ssl Installation Instructions

Asa Basic Configuration Networking Fun
Using Firewall Builder To Configure Cisco Asa Pix Page 4 Page 4

Ms Chapv2 And Radius Sp Initiated For Cisco And Netscaler Configuration Guide Secureauth Guides Global Site
Asa 8 3 And Later Monitor And Troubleshoot Performance Issues Cisco

Cisco Asa Firewall Fundamentals Part 1 Dave On Security
Cisco Security Cisco Asa 5505 Interfaces Configuration For Access Ports

Cisco Asa Interface Card Asa Ic 6ge Sfp B On Sale At Hummingbird

Step By Step Guide To Setup Remote Access Vpn In Cisco Asa5500 Firewall With Cisco Asdm

Cisco Updates Its Next Generation Firewall Management Application Prime Security Manager Cisco Blogs
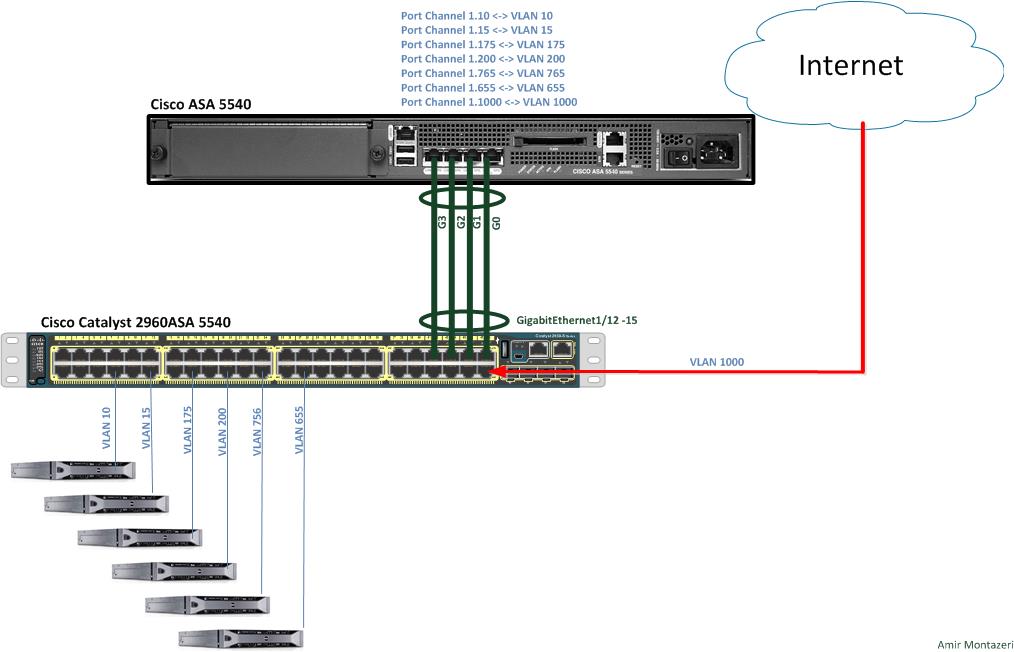
Etherchannel Port Channel On Cisco Asa Amir Montazeri

Configure Acl On Cisco Asa Firewall Tech Space Kh
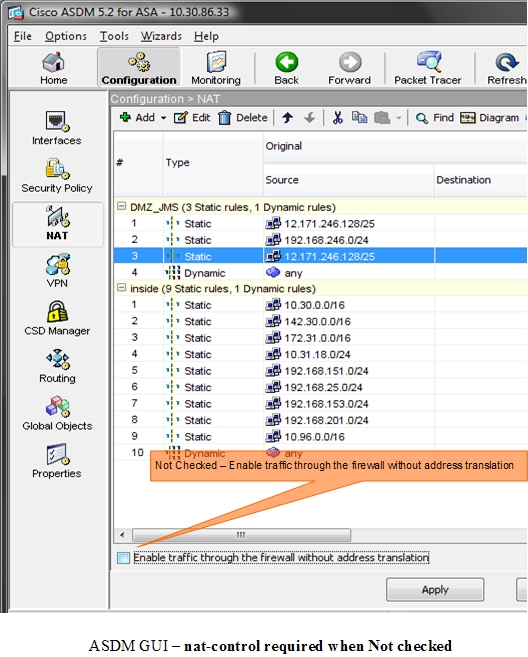
Check The Network Cisco Asa Firewall Best Practices For Firewall Deployment

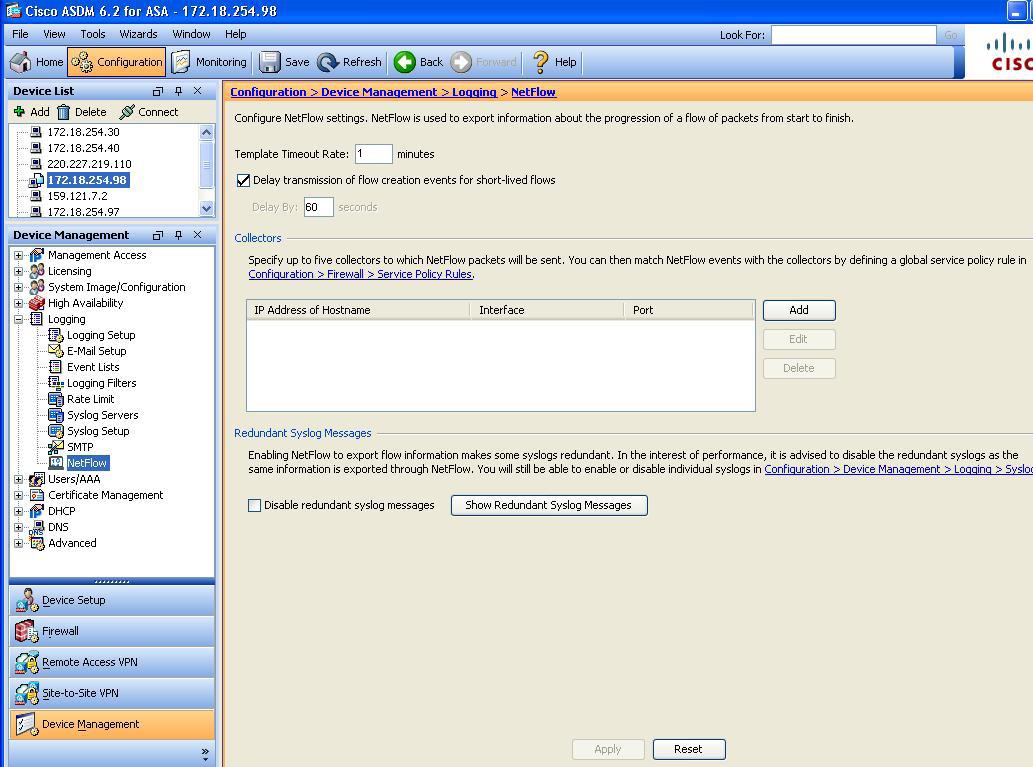
Configuring Netflow On A Cisco Asa Firewall Pathsolutions Support Portal
Cisco Asa 5515x Configuration
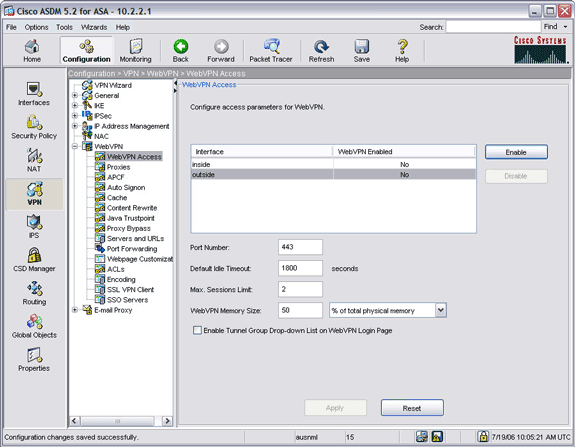
Ssl Vpn Client Svc On Asa With Asdm Configuration Example Cisco
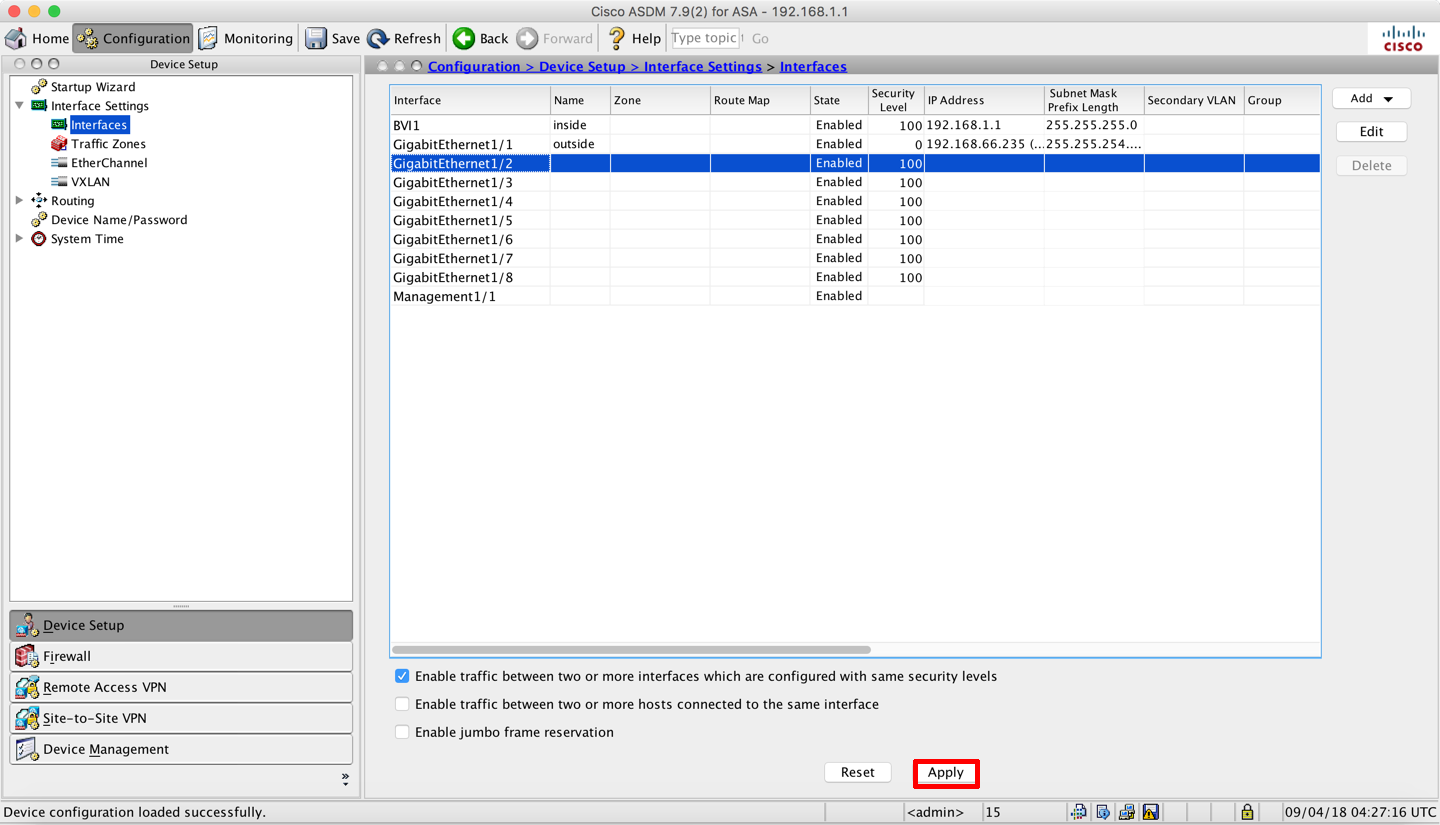
Cisco Asa 5506 X Bridged Bvi Interface Petenetlive

Cisco Updates Its Next Generation Firewall Management Application Prime Security Manager Cisco Blogs
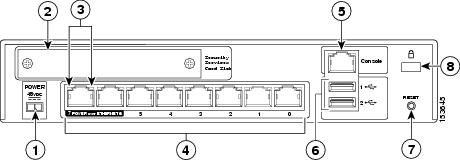
Cisco Asa 5505 Network Port Interfaces
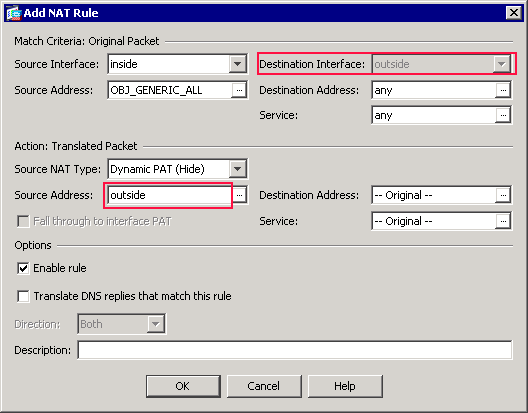
Asa 8 3 X Dynamic Pat With Two Internal Networks And Internet Configuration Example Cisco

How To Configure Vlan Subinterfaces On Cisco Asa 5500 Firewall

Firewalls Siem Fear And Loathing Of Log Savers

Lessons Learned Overriding Routing In Cisco Asa David Vassallo S Blog
How To Configure Cisco Asa 5505 Router For 8x8 Service 8x8 Support

Basic Asa Configuration Cisco Firewall Configuration Fundamentals Cisco Press
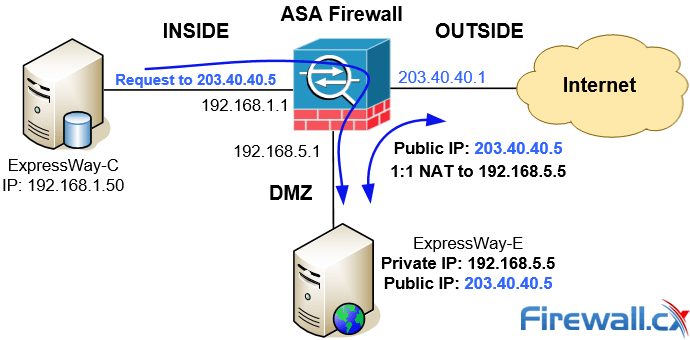
Understand Configure Nat Reflection Nat Loopback Hairpinning On Cisco Asa 5500 X For Telepresence Expressway And Other Applications

How To Configure And Get Started With Cisco Asa5505 Michaelriccioni Com

Step By Step Guide To Setup Remote Access Vpn In Cisco Asa5500 Firewall With Cisco Asdm

Cisco Failover Interface In Waiting Network Engineering Stack Exchange

Cisco Firewall Asa5508 K9 8 X 1 Gigabit Ethernet Interface 1 Management Port For Sale Cisco Asa Firewall Manufacturer From China
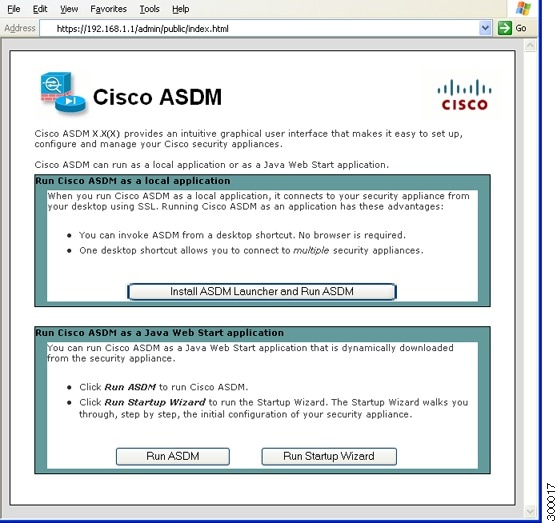
Cisco Asa 5505 Quick Start Guide Cisco
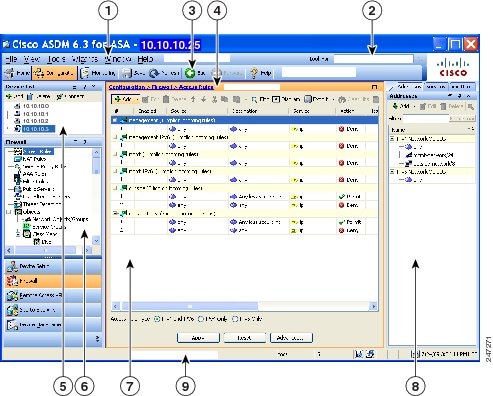
Asdm Book 1 Cisco Asa Series General Operations Asdm Configuration Guide 7 4 Asdm Graphical User Interface Cisco Asa 5500 X Series Firewalls Cisco
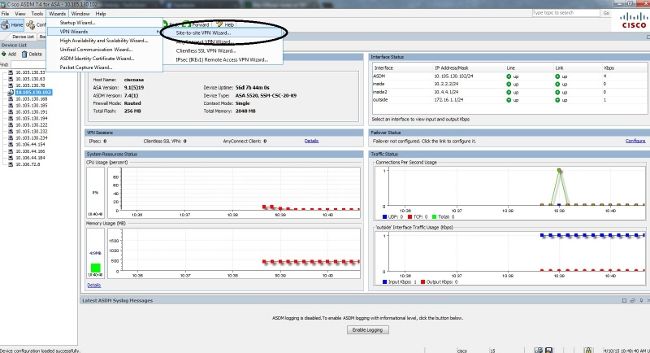
Configure Ikev1 Ipsec Site To Site Tunnels With The Asdm Or Cli On The Asa Cisco

Cisco Asa Failover Redundant Interfaces Catalyst Hsrp And Power Www Com

Cisco Asa Interface Card Asa Ic 6ge Cu C On Sale At Hummingbird
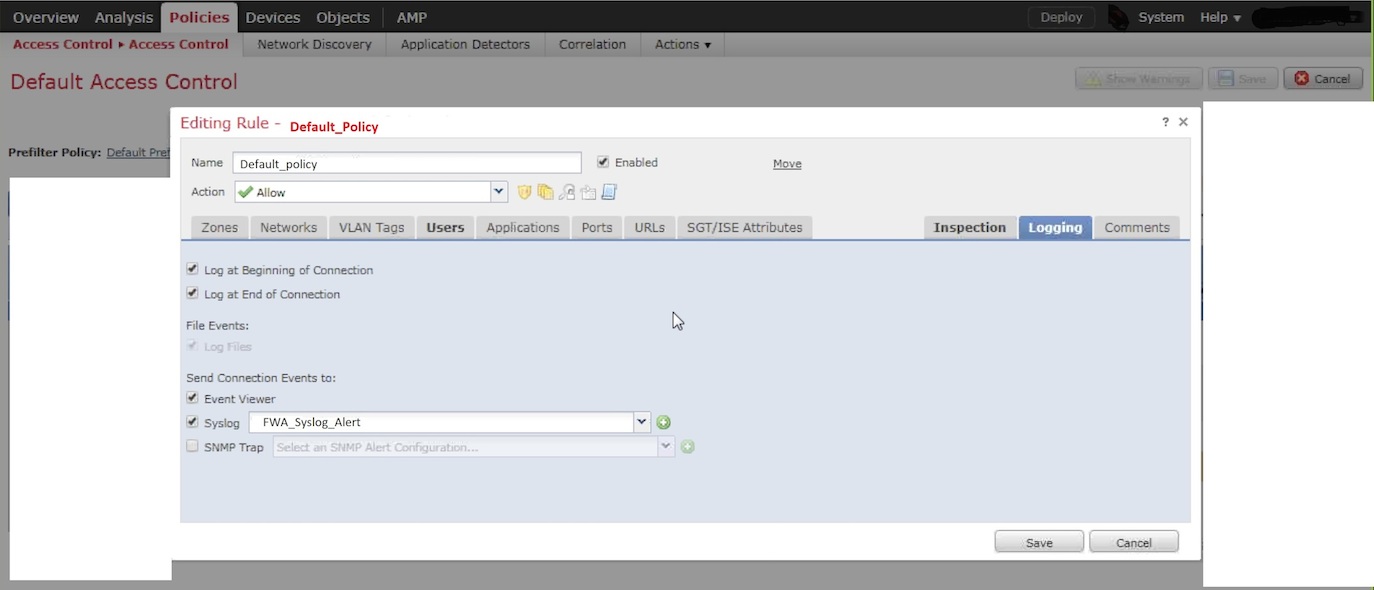
Configure Cisco Firepower Firewalls Forward Syslog Firewall Analyzer
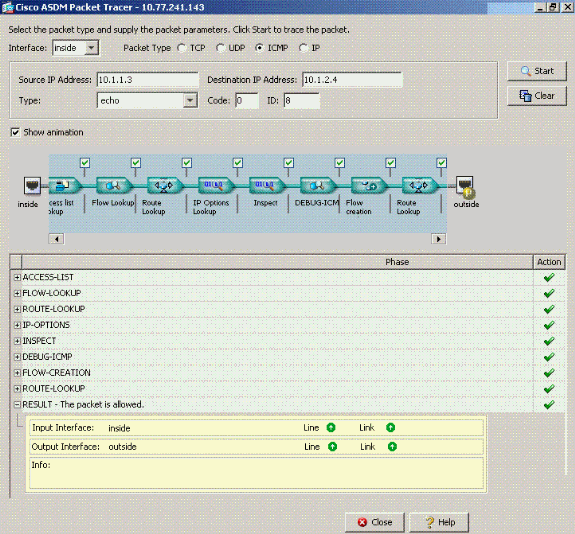
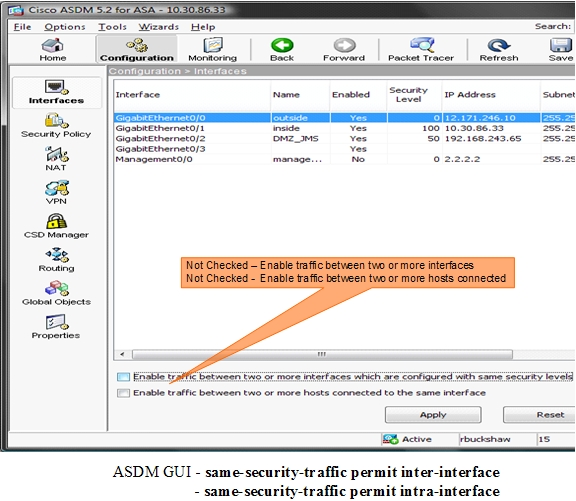
Pix Asa 7 2 1 And Later Intra Interface Communications Cisco
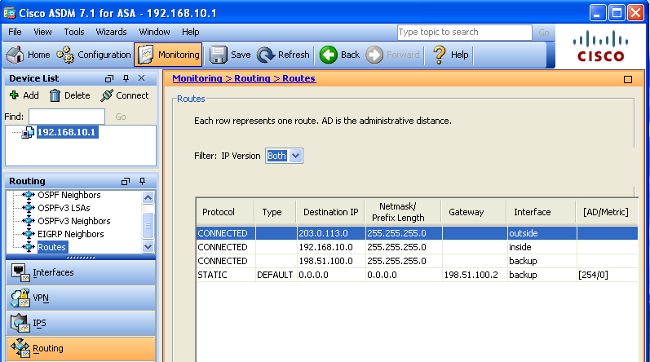
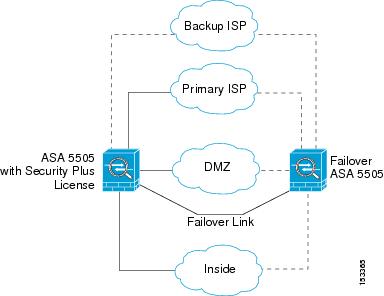
Configure The Asa For Redundant Or Backup Isp Links Cisco
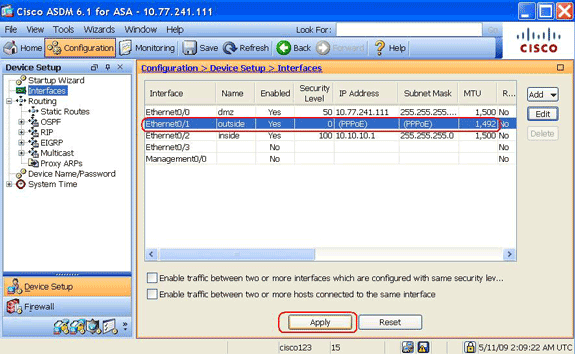
Pix Asa Pppoe Client Configuration Example Cisco

How To Check If Nat T Is Enabled On A Cisco Asa Support Home
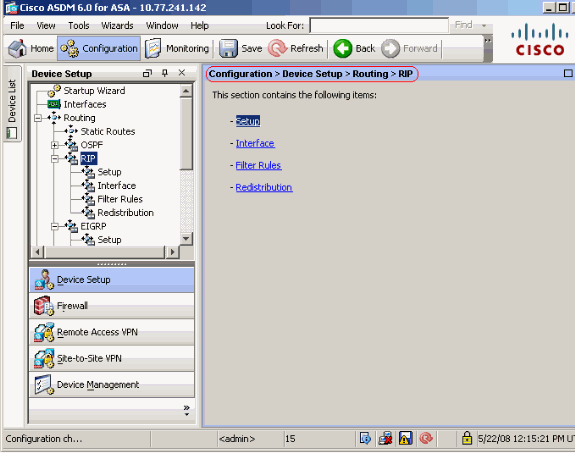
Asa Pix With Rip Configuration Example Cisco
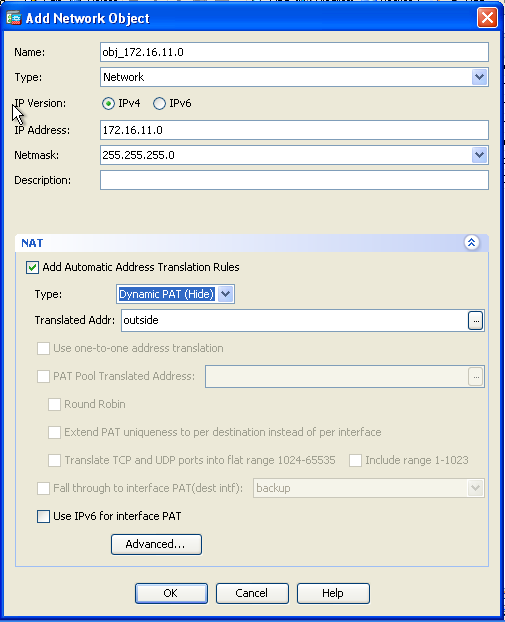
Configure Asa Version 9 X Port Forwarding With Nat Cisco
Cisco Next Generation Firewall Ngfw Demo Youtube
Cisco Asa 5505 Firewall Initial Setup Part 1 Youtube
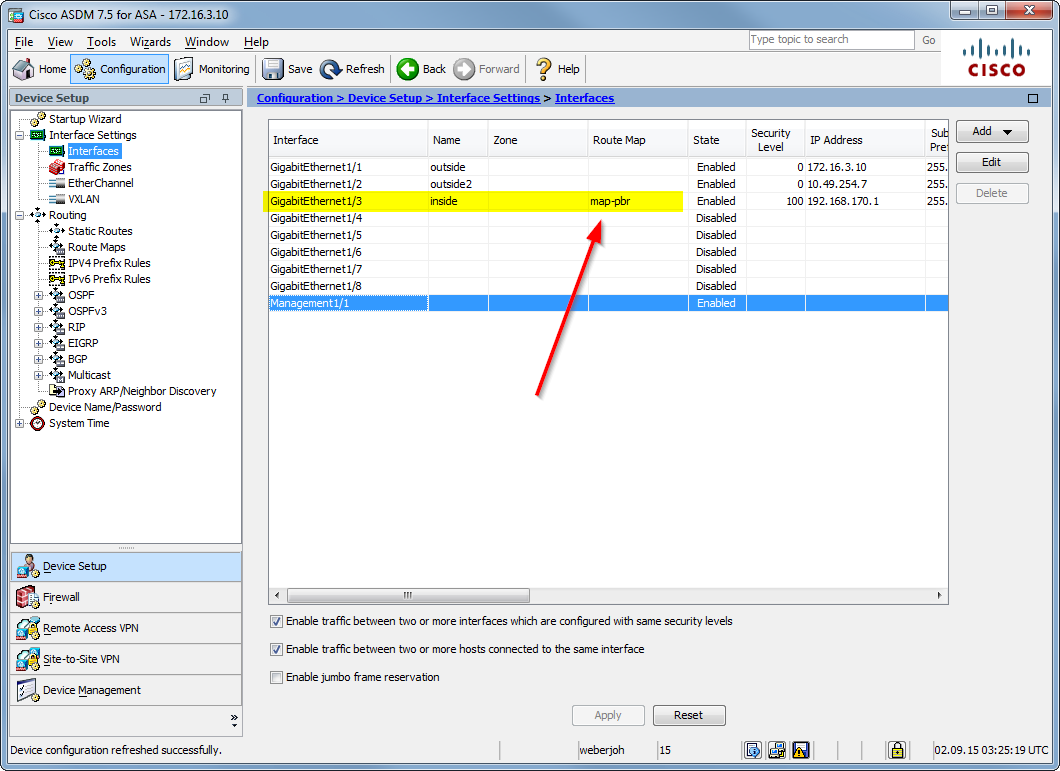
Policy Based Routing On A Cisco Asa Weberblog Net
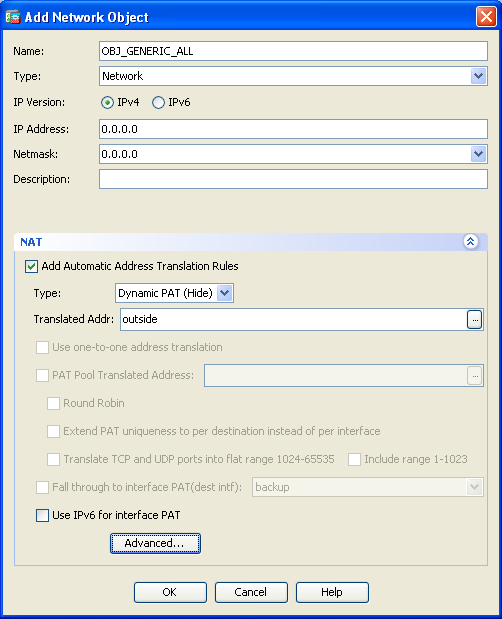
Configure The Asa For Dual Internal Networks Cisco

Cisco Asa Configure System Settings Interfaces Hostname Dns Password Time Ntp P1 Youtube
Cisco Graphical User Interface Gui Basics Dummies

Cisco Asa Initial Configuration Configure The Management Interface By Clarence Subia Medium

Cisco Asa Setting Up Port Forwarding Using Asdm Minecraft Example Islandearth
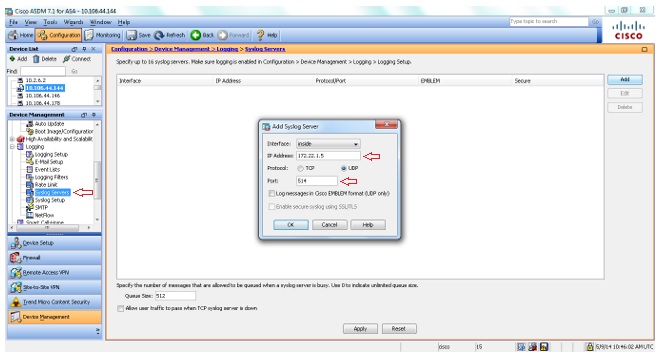
Configure Cisco Firewalls Forward Syslog Firewall Analyzer
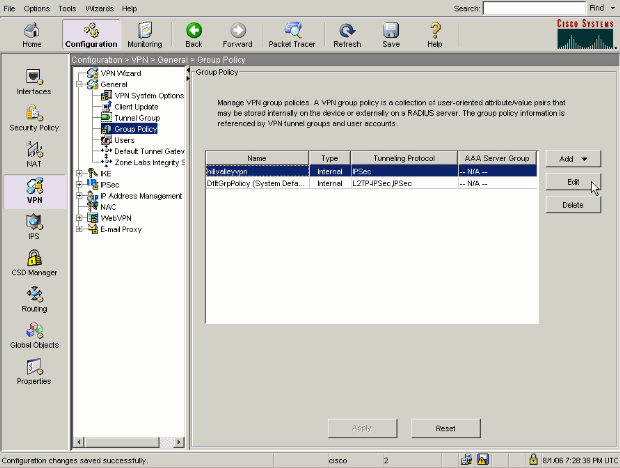
Asa Pix Allow Split Tunneling For Vpn Clients On The Asa Configuration Example Cisco
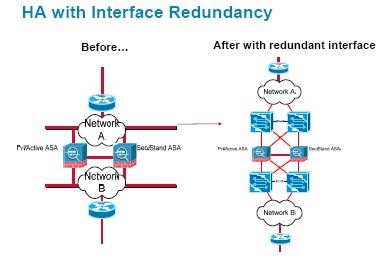
Cisco Firewall Design And Deployment Booches Nl
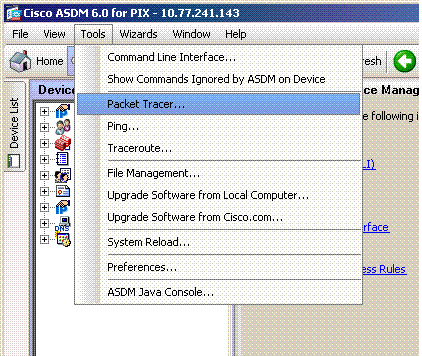
Pix Asa 7 2 1 And Later Intra Interface Communications Cisco
Cisco Service Ready Architecture For Schools Design Guide Security Design Design Zone For Education Cisco
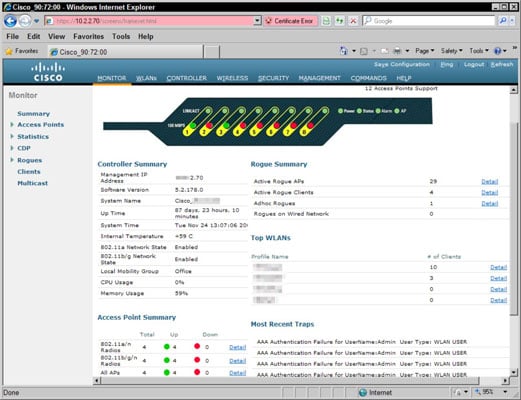
Cisco Graphical User Interface Gui Basics Dummies
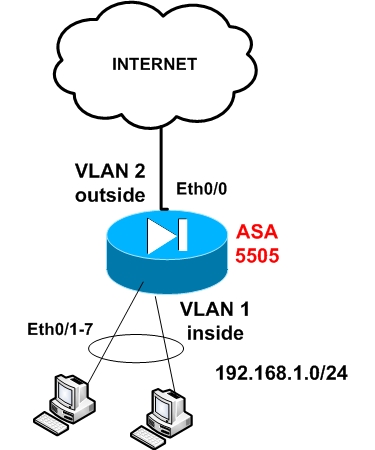
How To Configure Cisco Asa 5505 Firewall Router Switch Blog
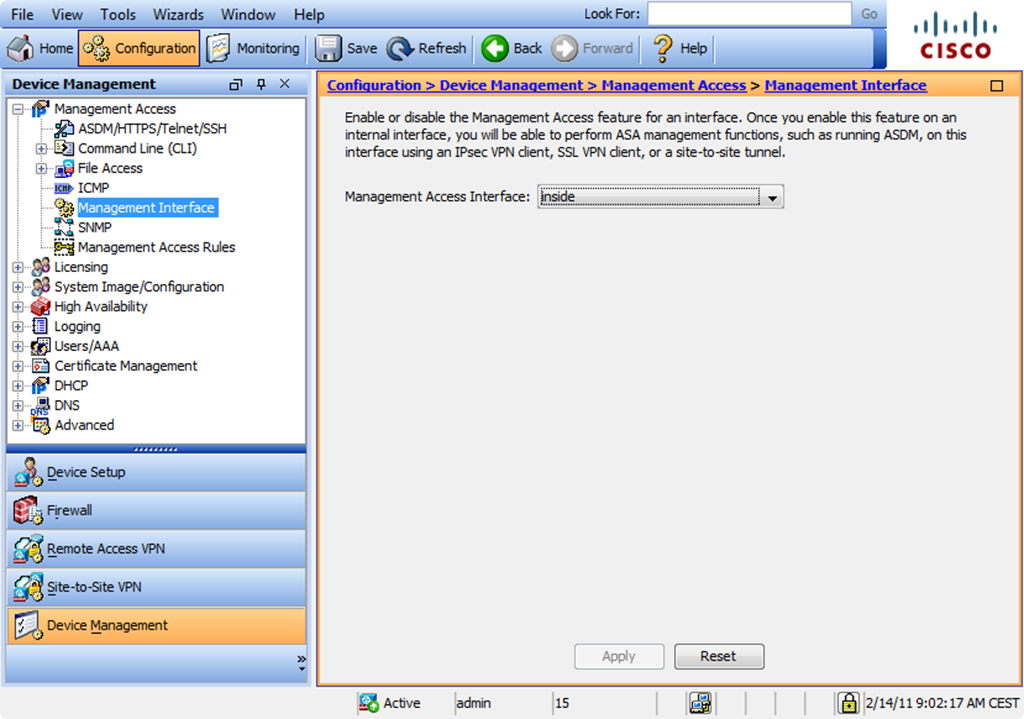
Cisco Asa Remote Management Via Vpn Booches Nl
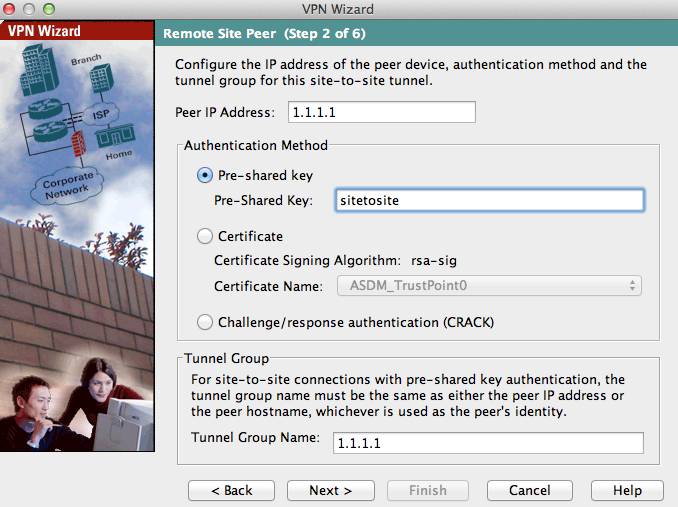
Mx To Cisco Asa Site To Site Vpn Setup Cisco Meraki
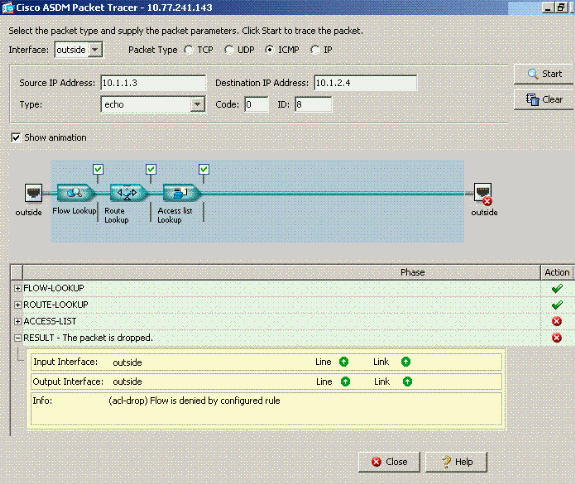
Pix Asa 7 2 1 And Later Intra Interface Communications Cisco

Configuring Cisco Asa And Pix Firewalls Part2

How To Set Up A Cisco Asa Dmz Cisco Asa Training 101 Youtube
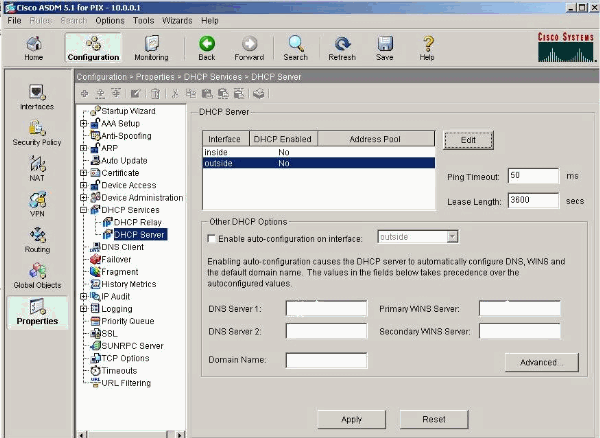
Pix Asa As A Dhcp Server And Client Configuration Example Cisco
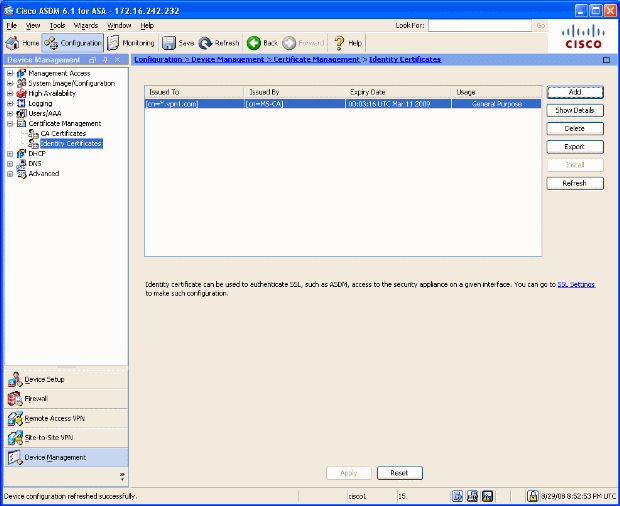
Asa 8 X Renew And Install The Ssl Certificate With Asdm Cisco

Gns3 Lab Cisco Asa Asdm Configure Tftp And Setting Up Of Loopback Adapter Sagar Networking Courses
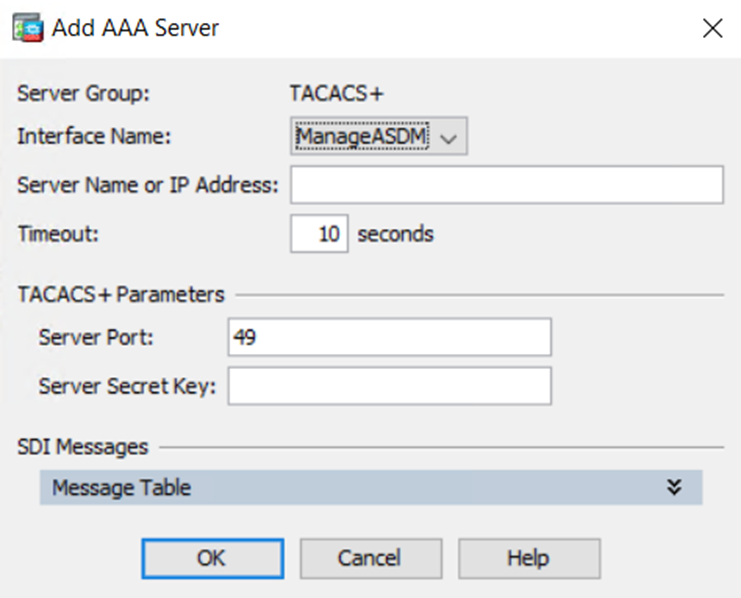
Cisco Asa Firewall Hardening Dionach



